The security needs of businesses have come to be much more critical than ever before. With constantly-evolving market space and other day-to-day challenges, all businesses need to stay up-to-date with all security aspects. At DNA Growth, we understand the criticality of the matter and thus ensure that all security concerns are under constant check.
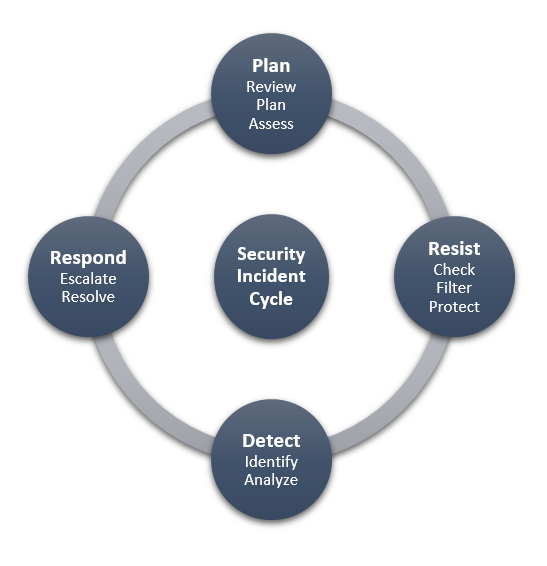
DNA Growth has a rigorous Security Incident Policy for security matters of all kinds. We like to plan our Security Incident Cycle meticulously which involves: